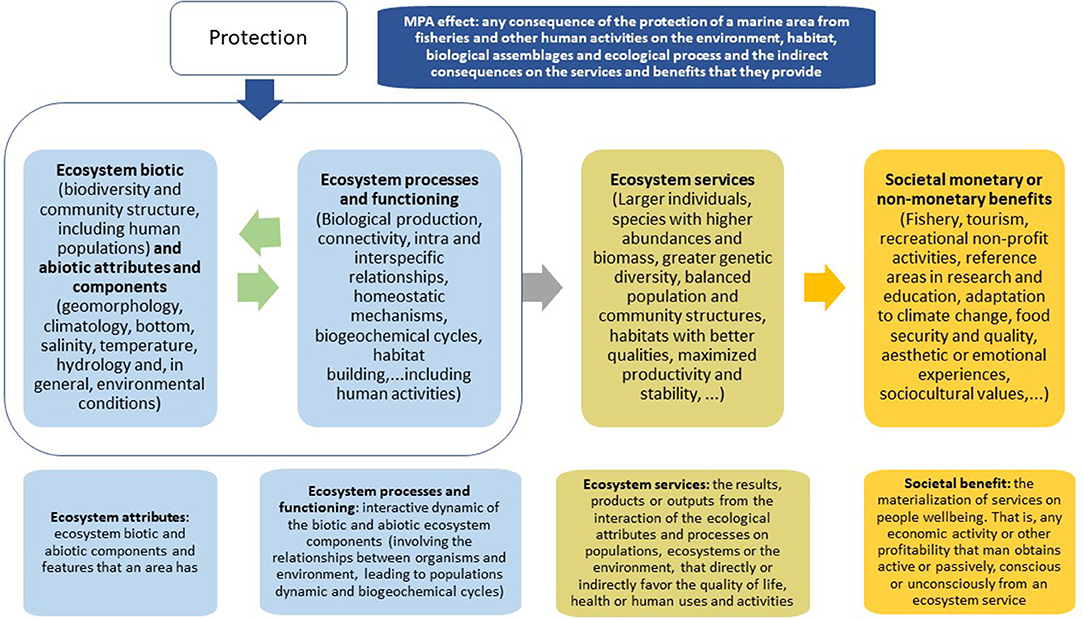
Frontiers | Reviewing the Ecosystem Services, Societal Goods, and Benefits of Marine Protected Areas | Marine Science
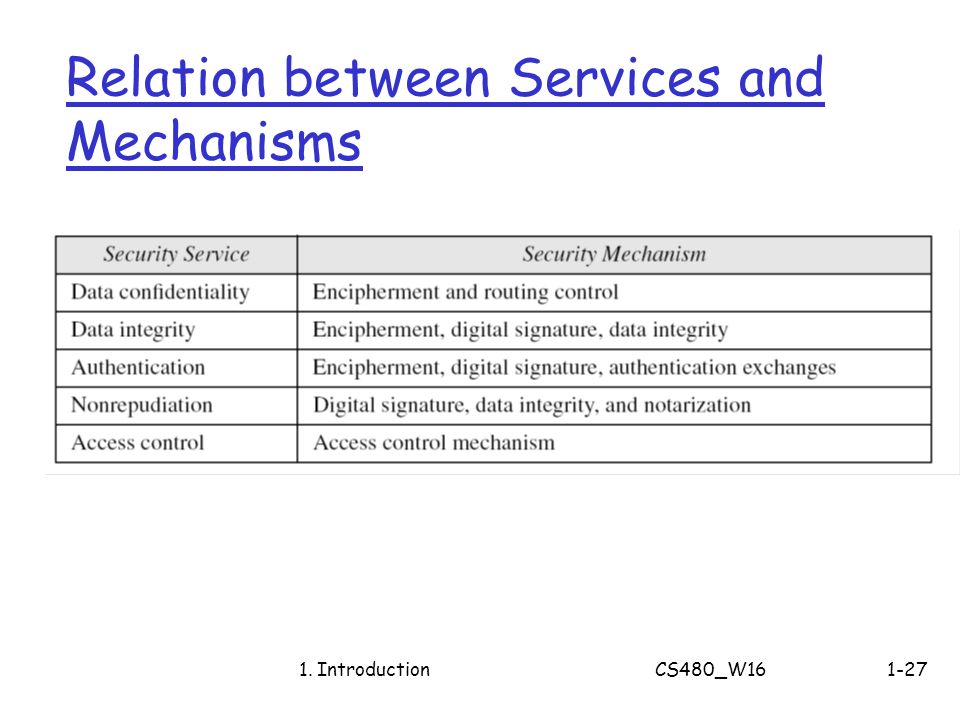
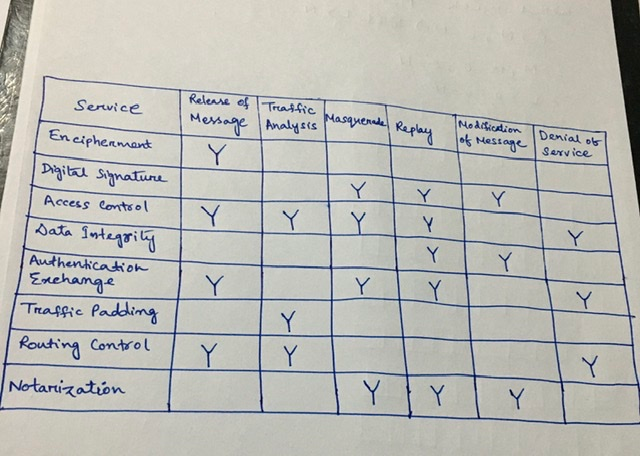
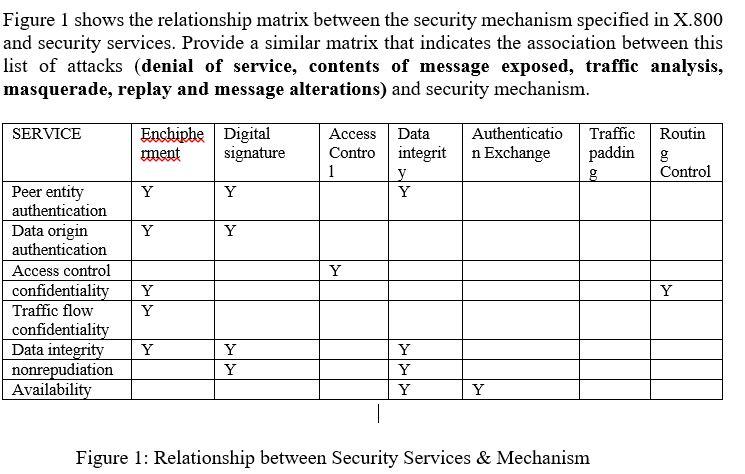
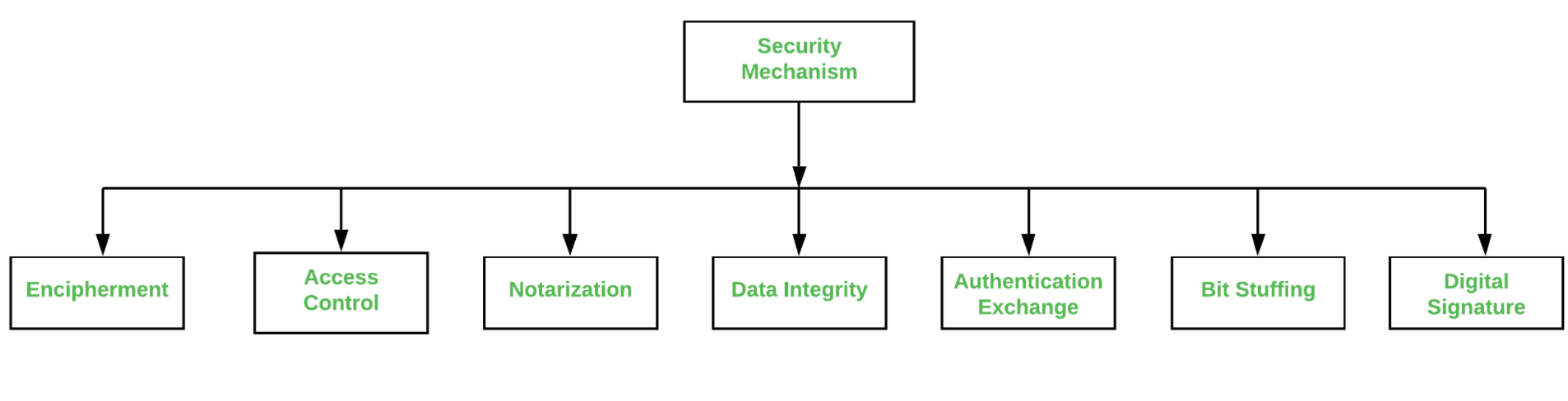
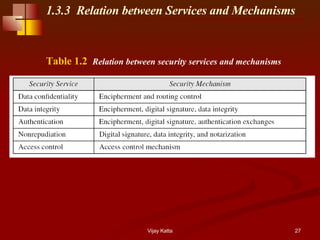
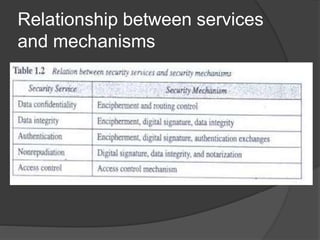
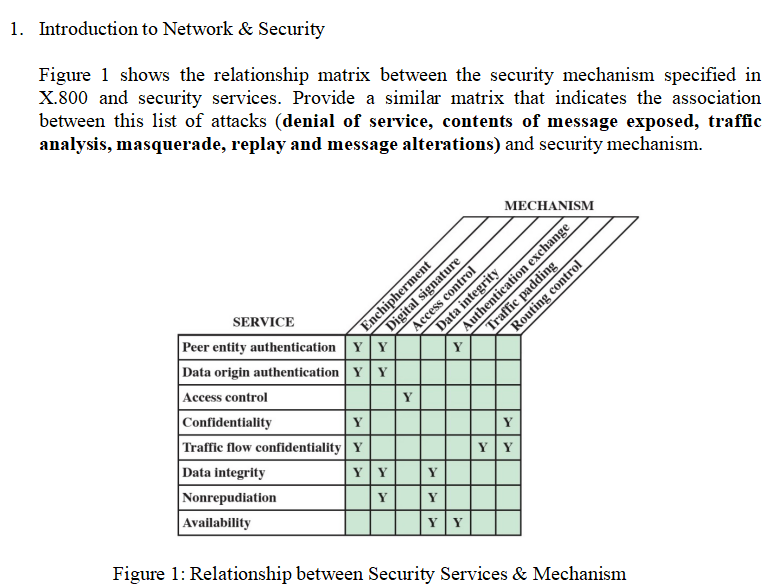
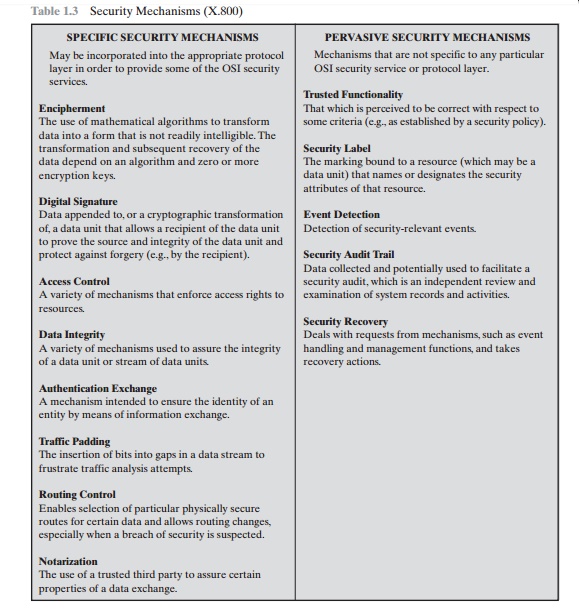
CS480 Cryptography and Information Security Huiping Guo Department of Computer Science California State University, Los Angeles Course administration. - ppt download
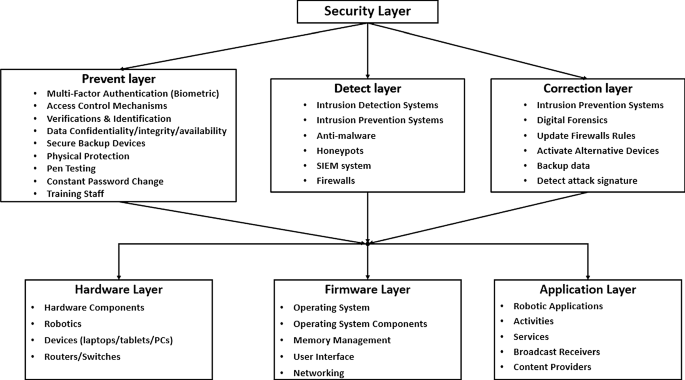
Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations | SpringerLink
Assignment1.docx - 1 Consider a desktop publishing system used to produce documents for various organizations a Given an example of a type of | Course Hero

General Security and Privacy Mechanisms for Liberty Identity Web Services Framework | Protogenist Blog